What is mobile banking and how does it work? Perhaps, you have been using your phone a lot in banking services and operations. For example, paid for stuff, transferred money, and opened up a deposit account. Or even subscribed to your bank's news and updates. This is mobile banking: every money operation you do with the help of a banking app on your phone.
Are you aware of the mobile banking security issues and the risks involved? Most of the letters you receive in your mail might also be malicious! Thus, you must protect yourself from potential threats lurking in your mailbox and learn how to solve the risks of mobile banking. If you still don’t know there are hackers phishing for your money or information, watch out and read on!
- New Generation of Mobile Banking
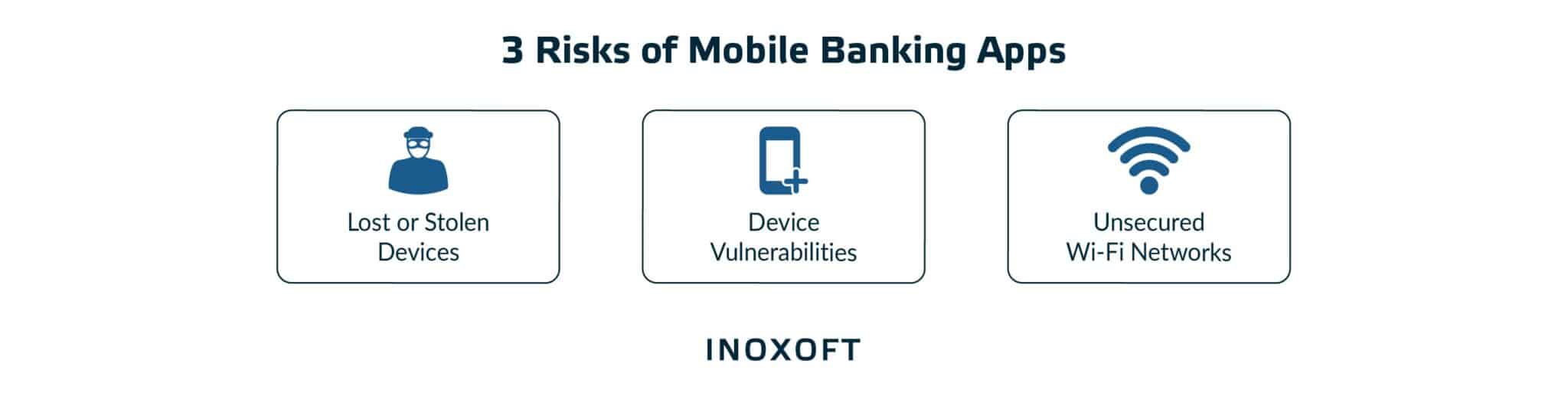
- 3 Risks of Mobile Banking Apps and How to Solve it
- Risk #1: Unsecured Wi-Fi networks
- Risk #2: Lost or stolen devices
- Risk #3: Device vulnerabilities
- Cyber Fraud and Digital Hacking
- The threat of Trojan Malware
- Best practices for mobile banking security
- Phishing
- Keyboard logs
- Man-In-The-Middle Attacks
- Mobile SIM Card Swaps
- A Pleasant Bonus
- Final Thoughts
New Generation of Mobile Banking
Nowadays, it is hard to imagine your life without carrying out online payments. Mobile banking technology allows us to shop, pay bills, order food, and make banking operations through banking mobile apps. The advantages of mobile banking lie in online support 24/7, numerous services and operations you can perform from your phone, paperless and less time-consuming solutions, and secure and more personalized approaches.
The benefits of mobile banking excite not only customers but banks themselves as online services are cost-efficient and reduce the budget spent on offline banking. Such features of mobile banking attract new users daily. Especially in COVID-19 situation, where staying at home and being possible to carry out various operations is a necessity. As the future of pandemics is still vague, there is a need for further mobile banking development. The more banks can provide online services, the better are their chances to adapt to the digital world and survive here.
The opportunity to use your mobile app for banking to carry out different tasks requires you to be protected from possible cyber-attacks and fraudulent actions that compromised mobile banking security. Have you ever received a suspicious email from your bank? Or downloaded a third-party app that required lots of permissions? Or went on websites, which asked for too much of your personal information? Then you know the mobile banking risks I am talking about. And this is no fun as in the end, you may get robbed by criminals, who might get your sensitive information or a big sum of money.
Read more: security vulnerabilities in web applications
3 Risks of Mobile Banking Apps and How to Solve it
From data breaches to fraudulent activities, the risks of using mobile banking apps can expose users to financial and personal security threats. We’ll explore the potential risks of mobile banking and discuss effective solutions to mitigate them.
Risk #1: Unsecured Wi-Fi networks
Public networks, aka free Wi-Fi hotspots, are most likely to become a breeding ground for scams and cyberattacks. Scammers intentionally target unwary users who connect to these networks, highlighting substantial mobile banking security issues.
One common tactic used by hackers is the creation of unsafe Wi-Fi networks that closely resemble legitimate networks. Users connect to these fraudulent networks, and hackers intercept their data and credentials. As a result, they successfully gain unauthorized access to sensitive financial information
Solution
We recommend relying on trusted and secure networks, such as your home or personal hotspot, to ensure the security of mobile banking. Virtual private network (VPN) will provide an extra layer of encryption and protection to your mobile banking activities.
Risk #2: Lost or stolen devices
If you keep your mobile device unlocked, a person who gains physical access to it can easily retrieve valuable data from it. They can access your mobile banking services, and exploit the stored data for fraudulent purposes. A strong password, PIN, or biometric authentication are vital to prevent unauthorized access.
Even if you do lock your phone, skilled hackers can exploit vulnerabilities in your device’s operating system or weaknesses in mobile banking apps. This leads to unauthorized transactions or even the misuse of payment methods like Apple Pay or Google Pay without unlocking your phone.
Solution
Set up a strong password or biometric authentication on your device to prevent unauthorized access. Pro tip is enabling remote tracking and data wiping features to protect your data in case of loss or theft. Don’t forget to contact your bank immediately to report the incident and deactivate access to your mobile banking app.
Risk #3: Device vulnerabilities
Device vulnerabilities pose significant security risks of mobile banking, potentially leading to unauthorized access to personal data. For example, failing to update the device’s operating system and apps can make it more vulnerable to malware assaults. Many updates include essential security patches that address vulnerabilities that could be exploited by hackers. This way, outdated software is generally easier to hack, which makes it important to install updates promptly, particularly for mobile banking apps.
Solution
To prevent such risks of mobile banking apps as malware, install reliable antivirus software on your mobile device. Keep your device’s operating system updated to address security vulnerabilities. You should also set up strong passwords or biometric authentication for accessing your mobile banking app.
Cyber Fraud and Digital Hacking
The secured network has become one of the largest segments that was heavily invested in and received 5.4 billion of revenue. Banks felt the desire to advance banking app security and make banking apps safe for the sake of their customers and themselves. But is mobile banking safe? Are banking apps safe? At present, among the most popular ways of getting to your mobile banking app are:
- Virus attacks
- Phishing
- Keyboard logs (keyloggers)
- Man-in-the-Middle attacks
- Mobile SIM card swaps
All of these attacks harmed mobile banking security in one way or the other. Thus, a need for better security provision and banking security solutions promised to obtain better mobile banking app features. Cybercriminals always were and will be. And, with the new generation of tech-savvy consumers, cyber fraud became tech-savvy as well.
Spending on worldwide cybersecurity has reached $71.68 billion in 2022, which is quite understandable. To ensure, that none of the mentioned methods will work on you and your mobile banking app, it’s time to be cautious.
The threat of Trojan Malware
The reason for being prudent here lies in the mobile app malware called Trojans. Of course, the bank has given you a link to the official banking app. But hackers never sleep and have made a fake program. And while you search for the official one, you are being redirected to a third-party site with a similar app or find a malware program identical to the bank’s app. At least, identical at first sight. The only difference is the program’s origin.
But how could you tell if this isn’t the first thing you look at? Hence, there’s malware uploaded or other spyware apps from third-party sites.
Discover the best practices of gamification in banking industry
Trojans work either on the surface or are hidden underwater. At first, Trojans make you believe in their good intentions. Even if a Trojan is not suspicious, it steals the data from your bank account, e-payment, and credit/debit card. All of it, in a few seconds! To add, Trojans copy, delete, change, or block your info, leaving the app disrupted or unable to be used. While you guess what’s wrong with the app and how to fix it, Trojans send your data to hackers. And, there you have it – they have access to your bank account and operations.
The other way around to install a Trojan is to get an app that has this malware within it. The minute the app is installed, the Trojan searches for a banking app within your phone. Then, when you’d like to check your credit card balance or make another kind of operation online with the help of your app, the Trojan simulates the first page where you enter your login and password. It isn’t fair, but you will never notice it was substituted, and will surely enter your password and login into the malware fields.
Best practices for mobile banking security
The truth hurts – in this case, all your sensitive data goes directly to the cyber hacker and you got your bank account hacked through your phone. In different cases, some of the Trojan malware can ask for permission to read your messages during the installation process. Essentially, the hacker will need a confirmation code. But the cyber thief will never get it unless you press ‘allow’. Therefore, there is a strong need to protect yourself. The best you can do to mobile banking safety is to:
- download apps from the Play Store only
- have an eye for details: download rate, app feedback, etc.
- give out fewer permissions to programs
- never install apps from third-party sources
- install an antivirus app
App Stores always check how secure are banking apps on their platform. If the latter weren’t secure, they would not have been displayed in the app store. Also, always check such details as the download rate and customer feedback as these might save you time and extra effort, which come together with fraudulent app installation. To add, allow programs to use your mobile programs and data less. For example, allowing a program to read your messages and have access to your contacts won’t lead to security in mobile banking. Eventually, it will compromise your safety.
Phishing
The thing about awkward emails with suspicious links has taught us not to open them anymore. 27.7% of phishing attacks aimed at financial institutions globally during the fourth quarter of 2022. Although people are becoming more cautious, hackers invent newer ways to catch the inattentive ones. The most common way to do so is to send an email to someone from a trusted source.
For example, the trusted source is your bank manager. Here, it is impossible to spot scams as the hacker will never give out his identity. You will be forced into thinking you’re communicating with a bank employee. And when the email asks to click on the link – why wouldn’t you? Especially, when the latter speaks about possible cyber-attacks and means to protect your money by following the unfortunate link. This action may cause you a big money loss or data leakage.
Hence, to protect yourself from these emails (most of them are caught in the spam folder), try to:
- verify the email address at the official site of the bank
- call your bank manager and ask whether there are troubles with your account (there aren’t any, be sure!)
- unsubscribe from bank news and never open such emails
Most of the emails with important updates from the bank are sent to your banking app directly. There you can read everything and feel safe. The email address hackers use may vary significantly from the one on the official site of the bank or may have only one dissimilar numeral or letter. So, it’s better to check twice: better safe than sorry!
Also, always visit your local bank or call your manager if you’d like to find out about your bank account, cards, deposits, etc. This information cannot be disclosed in the letter and, surely, is never there when you follow untrusted links.
Keyboard logs
Using a keyboard is not a new way to spy on sensitive content. But it is surely the most silent one. Downloading different keyboards from untrusted sources may be unwise. For example, this includes all the Android users who can upload new colorful and functional keyboards.
When you’ll need to log into your banking app, you will probably do that with the help of a new keyboard. But this way, you will give out all the info to the hacker with your own hands! If a cyber thief is having all that is needed to break into your account and steal money, there are little chances he wouldn’t do so.
Therefore, pose a question to yourself – do you need to install that keyboard? Not to fall for the keyboard fraud, you might:
- never download keyboard themes for your phone
- never allow the installed keyboard to be used when you enter confidential data
- install a good antivirus app to spot fraud
- enable two-factor authentication method to your bank account
If your freshly-uploaded keyboard is infected with malware, the best option is to have an antivirus app that spots these kinds of malware. Also, if you want to personalize your phone keyboard, you may do so, but be sure not to use it while entering passwords and logins. For this reason, some of the smartphones suggest using the integrated system keyboard as it is more confidential and secure.
Man-In-The-Middle Attacks
When the bank hackers desire to obtain your money, nothing will stop them on their way. For example, you will get an SMS that your bank account has been blocked and you need to call the bank operator to find out all the details. In these cases, people start panicking and lose all their common sense. You call the number and the person on the other end talks to you exactly like a bank worker. This person is the man-in-the-middle or MITM.
The fake bank manager asks you for your bank account details, passwords, logins, CVV pin, and so on. So, practically, you receive the exact services you’d get at the bank. But the bank manager would never ask you about your credit card pin or bank account password – it’s not politically correct to tell this info to a third-party. Thus, in the end, you’ll get robbed of your money.
Even if you suspect something concerning the message and try to call your bank’s official number, the MITM intercepts this call and, this way, you still communicate with a thief. The most outrageous fact here is that hackers train themselves like bank employees and never lose their temper or speak with a higher pitch tone if they want to succeed in their malicious intentions.
Also, there is one more MITM thing called DNS cache poisoning. It may be hidden in the link to the official bank site in the SMS. By poisoning your DNS cache, you will be redirected to the clone site of your bank without the slightest notice it isn’t the real one and gives away all the potential information the hackers need. Tricky of them but bad for you! Not to be caught off-guard and lose common sense, try:
- not to call the number in the SMS
- not to follow any links in the SMS
- spot the number the SMS came from
- look at the current date and time (day and hour)
- visit your local bank personally
- never give out your private bank information
- bank managers never ask for your logins and passwords
- perform actions only via a secured network
- check HTTPS and the address bar
- do not use a public wi-fi connection
The number the fraudulent SMS comes from has nothing to do with official bank numbers. It is random. The date and time when you received this SMS are also important. As most of the thieves want to catch you off-guard, they will send an SMS at the weekend or out of the bank working hours. It is hard to understand these factors when you’ve read about your account being blocked, but these are of the utmost importance if you don’t want to fall into that trap.
Besides, there is no bank manager, who will ask for your private and sensitive information via the phone or even personally. Most of the banks remind their customers that they should not enclose such information in any circumstances
Mobile SIM Card Swaps
With the introduction of a two-step verification process, phone calls to authenticate the bank user, and fingerprints or face scanning to access your bank account, cyber thieves made up a new way to commit a crime. For example, the thieves make several calls to your phone, none of which you answer. Or even if you answer these calls, you will hear only silence. Then the hacker intentionally goes to the mobile service provider and says the phone has been lost together with a SIM card.
Unfortunately for you, the thief knows your last phone calls by heart. And, if your phone number has not been appended to your ID, the mobile provider has no objections to believing that this number belongs to the person in front of him/her. Thus, the mobile service provider renews the card number and gives it to the evildoer.
Once cyber hackers have your card number, they may change your logins and passwords to banking apps and get all your money. This way, SMS verification codes won’t bother them in trying to drain your account. But, here’s what you have to do:
- reinforce your mobile SIM card with your ID
- keep your sensitive information private
- find out if your SIM card provider has anti-hacking support
- if you experience multiple calls with no answer – be cautious
Always buy official SIM cards that go with a contract, where you put your ID information. This way, when the criminal is going to steal your SIM card number, he/she will have no chance to do so, as the mobile provider will understand it’s not you. Then, keep all the information that might be used against you or to receive your money, private. Privacy is the key to success. The fewer different people who know your sensitive information the higher is the level of your safety. Perhaps, your mobile provider has an option that you can sign up to and be protected from cyber hacks and cyber fraud.
A Pleasant Bonus
To make you feel on the safe side, here’s a list of the best antivirus apps in 2023. These antiviruses have been acknowledged by the New York Times, the Guardian, Forbes, C-Net, and Wired. The top 10 malware catching apps are:
- Norton
- Bitdefender
- TotalAV
- Intego
- Panda
- Kaspersky
- PCprotect
- McAfee Antivirus
- Avira
- BullGuard
To be sure risks of using mobile banking won’t hurt you, stay cautious, and never let yourself be distracted by the tricks of cyber hackers.
Final Thoughts
The article highlights the security risks of mobile banking applications and gives appropriate solutions to these concerns. We discussed three major risks and dangers of online banking: unprotected Wi-Fi networks, lost or stolen devices, and device vulnerabilities. Still, the prevalence of cyber fraud and digital hacking doesn’t end there: we need to keep an eye on various methods used by cybercriminals, including virus attacks, phishing, keyboard logs, man-in-the-middle attacks, and mobile SIM card swaps.
By following best practices against the security risks of mobile banking and utilizing reliable antivirus software, users can enhance their mobile banking safety and protect themselves from cyber threats. And naturally, partnering with a reliable vendor can assist banks in meeting the modern requirements for a banking system with enhanced security.
Being an international software development company, Inoxoft offers banking software development services to help banks and financial companies enhance their operations and provide an improved customer experience while ensuring security. We implement advanced security measures, including AI-powered fraud prevention, regulatory compliance, and robust authentication schemes to protect against financial crimes, fraud, and money laundering.
Choose Inoxoft for your banking software development needs and receive a dedicated team of experienced developers who can implement advanced software solutions, automate processes, improve customer experience, and prioritize security and compliance. Contact us to discuss how Inoxoft’s banking software development services can provide you with a highly secure solution.
Frequently Asked Questions
Is mobile banking safe?
Yes, mobile banking is generally safe. Banks employ various security measures to protect your information and ensure secure transactions. Your data is encrypted and transmitted across banking channels with high security to prevent malware attacks. Additionally, banks implement safeguards like device authentication and six-digit PIN verification to enhance the security of mobile banking applications.
Are banking apps safer than websites?
Both options are generally secure as banks invest in the security of these services. Mobile banking apps are slightly safer in terms of security because they typically don't store any data. That reduces the risk of data breaches or unauthorized access.
Why should you use mobile banking?
Mobile banking offers improved customer experience, allowing you to access banking services 24/7 without visiting a physical branch. It saves time by enabling online bill payments and providing features like money transfers, high-level security, fraud alerts, and customer support. Monitor and manage your transactions, benefit from added services, and enjoy enhanced security measures.
To learn more about mobile banking in the article Advantages and Disadvantages of Mobile Banking
What are the risks of using mobile banking?
- Unsecured Wi-Fi networks: Public networks are often targeted by scammers, who create fake networks to steal users' data and credentials.
- Lost or stolen devices: Unauthorized access to sensitive accounts and information is possible if a device is lost or stolen, even with a locked device.
- Device vulnerabilities: Failing to update the device's operating system and apps increases the risk of malware attacks and security breaches.
How to solve the risks of mobile banking?
- Use trusted and secure networks, such as your home Wi-Fi or a VPN, for mobile banking.
- Secure your device with strong passwords or biometric authentication; enable remote tracking and data wiping features.
- Install antivirus software and keep your device's operating system updated.